I'm trying to reverse engineer the protocol that an old home alarm system uses to communicate with the keypads. Connected via 4 wires:
- GND
- 13.2V
- DATA
- CLOCK
I've managed to connect the wires to a logic analyser. Here's a snapshot of a periodic data packet that it sends:
(Top is CLOCK and bottom is DATA)
Based on observation of the packets it appears that the first part (slower clock) is the keypad sending data to the panel and the second part is the panel reporting status (sending data to keypad).
Does this protocol look like anything standard? I've tried different analysers in the Saleae Logic software, but nothing seems to output anything meaningful.
UPDATE:
I've disconnected keypad's data and clock wires and can see that the clock and the data is generated by the panel (the output is the same as on the above screenshot).
Here's what the signal looks like on large time scale:
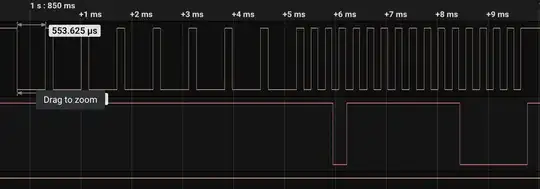
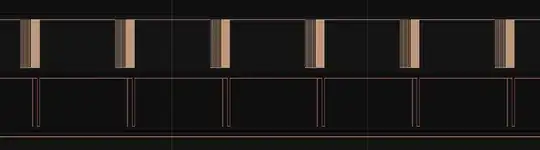
I've disconnected keypad's data and clock wires and can see that the clock and the data is generated by the panel (the output is the same as on the above screenshot).
– Muxa Jul 02 '22 at 01:26