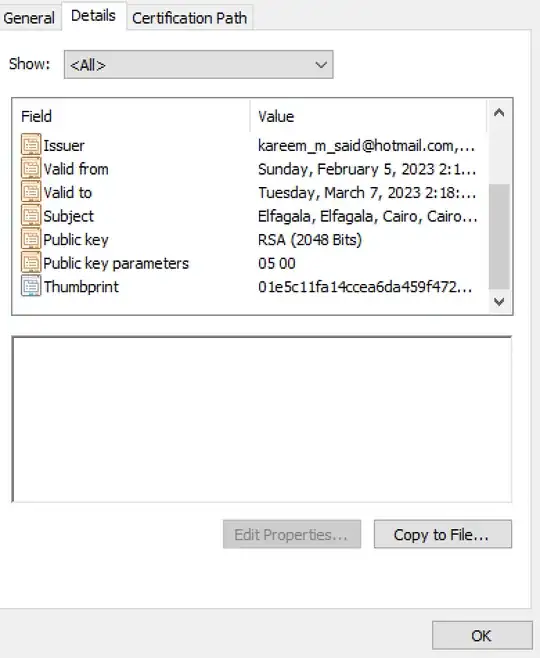
I have been trying to create a self-signed certificate with subject alternative name; however, although the cretifcate was created successfully, SAN was not added to its details.
Here's the command I used to create singing request.
openssl req -newkey rsa:2048 -nodes -sha256 -keyout server.key -out server.csr -config openssl-san.cnf
And here's the content of the configuration file.
[ req ]
default_bits = 2048
distinguished_name = req_distinguished_name
req_extensions = req_ext
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
stateOrProvinceName = State or Province Name (full name)
localityName = Locality Name (eg, city)
organizationName = Organization Name (eg, company)
commonName = Common Name (e.g. server FQDN or YOUR name)
Optionally, specify some defaults.
countryName_default = **
stateOrProvinceName_default = ****
localityName_default = ****
0.organizationName_default = ******
organizationalUnitName_default = **
emailAddress_default = *********
[ req_ext ]
subjectAltName = @alt_names
[alt_names]
DNS.0 = localhost
What am I doing wrong here?
Please note that I'm a software developer so creating certificates are not my typical thing