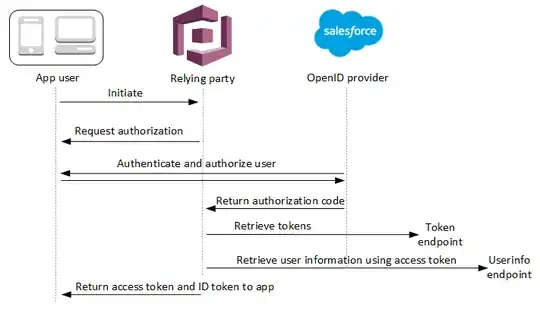
I don't understand why AWS Cognito require a client secret when configuring an external IdP (e.g. Azure AD).
AFAIK, AWS Cognito merely forwards federated identities to the external IdP for (OIDC) authorization code grant flows, which in turn results in access- and ID tokens issued to the app after successful authentication:
The client secret is only needed for AWS Cognito authenticating as a service towards e.g. the Azure AD app registration, but why is that needed?
https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-pools-oidc-flow.html