This question was originally posted to stack overflow, they suggested I repost it here (https://stackoverflow.com/questions/76715004/aws-nat-instance-setup).
I am currently learning the AWS cloud and decided to build the following architecture as a challenge:
- A VPC with a public and private subnet. The public subnet has access to the internet via an internet gateway.
- A NAT EC2 instance in the public subnet, that should act as a NAT gateway to allow instances in the private subnet access to the internet.
- An instance in the private subnet to test the internet connectivity.
I have the following documentation as a reference: https://docs.aws.amazon.com/vpc/latest/userguide/VPC_NAT_Instance.html
However after countless tries I was not able to allow the private instance access to the internet. I will outline all the steps I took. They should match those in the documentation.
- Create the VPC: use the aws console to create a default vpc with 2 subnets (1 public, 1 private) in 1 AZ.
All settings are as default, the NACL should allow everything, and the public route table points 0.0.0.0/0 to the igw, and both route tables point the vpc cidr to local.
- Create a private instance in the private subnet:
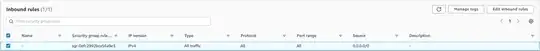
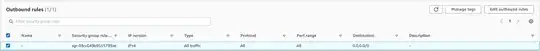
I used default settings except I selected the private subnet, did not assign a public IP, and used a custom securty group (troubleshooting-sg), which should allow everything (just to rule out the sg).
troubleshooting-sg:
- Create the NAT Instance:
I launch this instance in the public subnet, with AMI (Amazon Linux 2023 AMI 2023.1.20230705.0 x86_64 HVM kernel-6.1).
I set Auto-assign public IP to true.
I use the troubleshooting-sg.
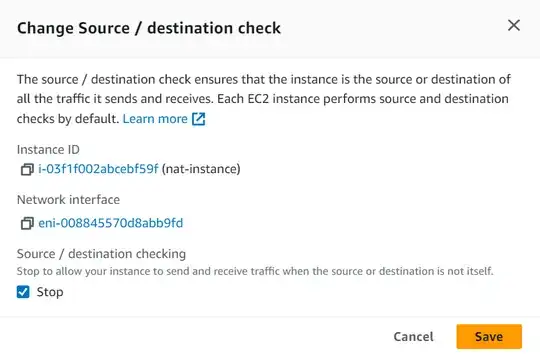
Upon creation I disable destionation/source checking in the networking configuration (this cannot be disabled in the creation panel, or I could not find it).
I ssh into the NAT instance in order to configure iptables. I run the following commands:
sudo yum update -y
sudo sysctl -w net.ipv4.ip_forward=1
sudo /sbin/iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
sudo yum install -y iptables-services
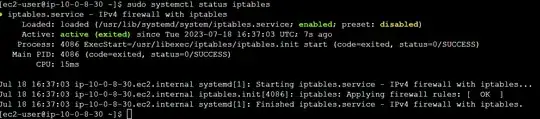
sudo systemctl enable iptables.service
sudo systemctl start iptables.service
The NAT instance configuration is done.
- Update the private route table to point to the NAT instance.
0.0.0.0/0 should be routed to the NAT instance.
Testing:
I ssh into the NAT instance. Internet access is verified.
From the NAT instance I ssh into the private instance using ssh keys.
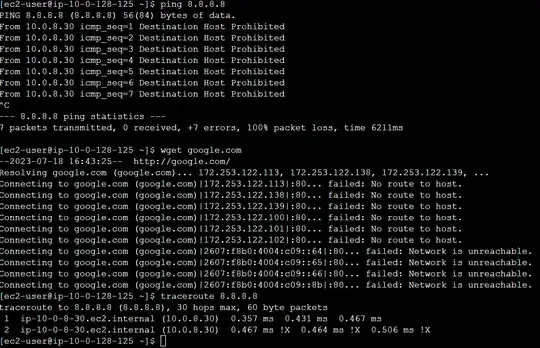
From this instance I don't have internet access:
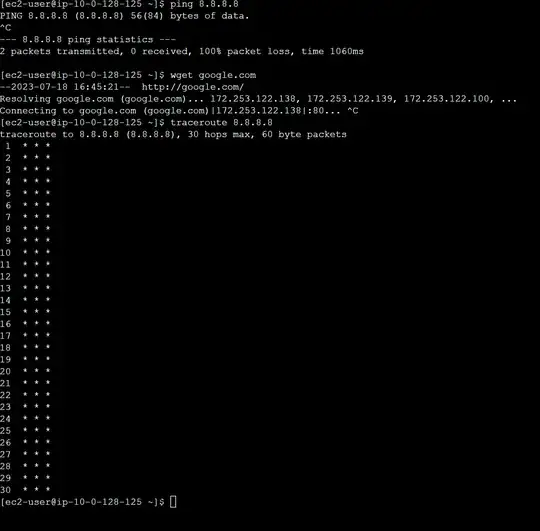
Just for reference, If I remove the NAT instance from the private route table I get the following:
I am not really sure how to continue. It seems the problem is the configuration for the NAT instance, but I have followed (I think) all necessary steps.
I would love some ideas on how to further troubleshoot this.
Thanks!