So my company is using Microsoft 365 (E5 license). And we're leveraging "Microsoft Defender Cloud App Catalog" to block access to some "cloud apps".
However, it turned out that some people actually need access to the blocked cloud apps, which is doable using Defender's "Device Group".
Unfortunately, it seems one endpoint device can only be a member of exactly one Device Group, no more, no less.
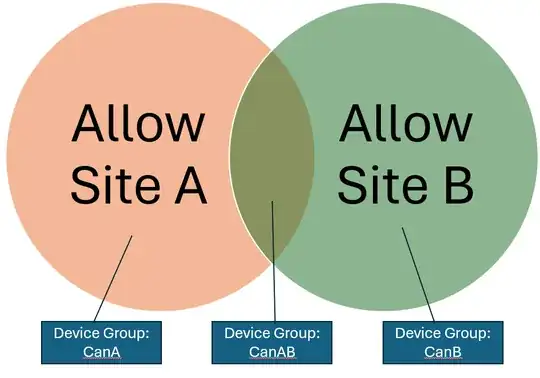
That led me to set things up like this:
Once I created the 3 Device Groups, on the "Unsanctioned" setting of Site A, I excluded the "CanA" and "CanAB" groups. Similarly for Site B, I excluded "CanB" and "CanAB" from the site's "Unsanctioned" settings.
Everything works acceptably, as expected.
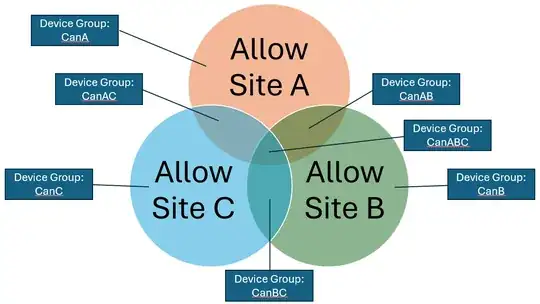
However, it came to pass that there is now a THIRD site that needs similar treatment. This means the relation is now like this:
This is such a complexity! Not to mention that if in the future a fourth site needs the same treatment, the number of groups will grow out of control.
Is there a better way to leverage Microsoft 365 to provide what I want?
(If a device can be a member of multiple device groups, of course this is easily solvable. But the fact is, a device can only be a member of exactly one device group.)