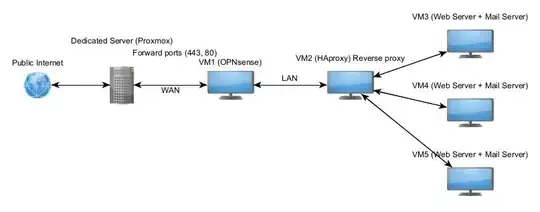
I'm trying to figure it out how to reverse proxy based on condition email servers or how to deal with sending/receiving emails from different servers on only 1 public IP address?
My current configuration is as below:
I have successfully managed to proxy web servers (OpenLiteSpeed) based on condition with OPNsense + HAproxy e.g. domain1.com -> Web Server1; domain2.com -> Web Server2; etc.
A records of every domain is pointed at my public IP address and web traffic is handled by OPNsense and HAproxy to specific local server based on conditions.
The problem is that i can't make it work to do the same thing with Postfix/Dovecot. So every mail server e.g. mail.domain1.com, mail.domain2.com etc. A record and MX record is also pointed at my public IP address but handled internally by separated server.
I know i can port forward, 25,465,993 etc. from my dedicated server to specific mail server but that works only at specific server and others will be unable to handle mails.
Any idea how to solve this?
I just read about that but not sure if it can work as it should ->
global
# ... (unchanged)
defaults
# ... (unchanged)
frontend email_frontend
bind :993 ssl crt /path/to/ssl_certificate.pem # IMAPS
bind :995 ssl crt /path/to/ssl_certificate.pem # POP3S
bind *:25 ssl crt /path/to/ssl_certificate.pem # SMTP
mode tcp
tcp-request inspect-delay 5s
tcp-request content accept if { req_ssl_hello_type 1 }
acl is_domain1 req_ssl_sni -i domain1.com
acl is_domain2 req_ssl_sni -i domain2.com
use_backend backend_domain1 if is_domain1
use_backend backend_domain2 if is_domain2
backend backend_domain1
mode tcp
server mail_server_domain1 172.16.0.2:993 check # IMAPS
server mail_server_domain1 172.16.0.2:995 check # POP3S
server mail_server_domain1 172.16.0.2:25 check # SMTP
backend backend_domain2
mode tcp
server mail_server_domain2 172.16.0.3:993 check # IMAPS
server mail_server_domain2 172.16.0.3:995 check # POP3S
server mail_server_domain2 172.16.0.3:25 check # SMTP