I have configured an Azure Kubernetes Service (AKS) with an Application Gateway in a private network setting. To facilitate communication between them, I've set up an Application Gateway Ingress Controller. There are no public IPs involved as everything is contained within a private network. I have established network peering between the Virtual Networks (VNets) of the AKS and the Application Gateway, in addition to peering from AKS to the Application Gateway and vice versa.
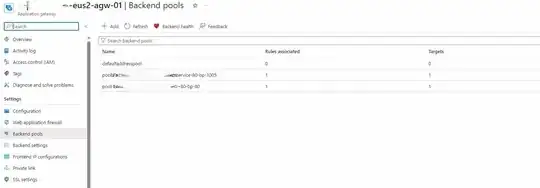
To test the ingress service, I deployed pods and set up an ingress component in one of these pods, marking the private IP setting as true in the configuration. I executed this configuration using the Kubernetes controller. Upon deployment, a backend pool was automatically added to the Application Gateway, indicating that the ingress controller is operational and the pod is running successfully. I have confirmed the functionality of the pod through tests.
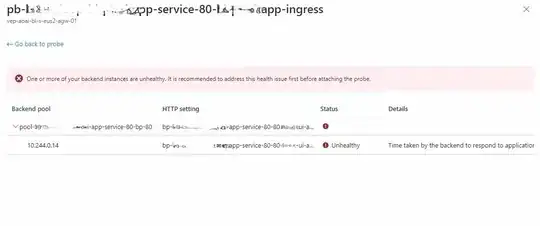
However, when I attempt to access the service via the private IP of the Application Gateway, I encounter a 502 error, suggesting that the Application Gateway is unable to communicate with AKS. I have verified that the backend pools in the Application Gateway are correctly mapped to the ingress of the pods.
What steps can I take to diagnose and resolve this 502 error?
ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: prd-pt-ui-app-ingress
namespace: prd
annotations:
kubernetes.io/ingress.class: azure/application-gateway
appgw.ingress.kubernetes.io/backend-path-prefix: "/"
appgw.ingress.kubernetes.io/use-private-ip: "true"
spec:
rules:
- http:
paths:
- path: /*
pathType: Prefix
backend:
service:
name: prd-pt-ui-app-service
port:
number: 80