I use a kubernetes Cluster set up with RKE2. I have the problem that when setting up Vector via Helm
helm repo add vector https://helm.vector.dev
helm repo update
helm install vector vector/vector --namespace vector --create-namespace
as in https://vector.dev/docs/setup/installation/package-managers/helm/
then the pods of my vector daemon-set fail to get created due to Pod Security Restrictions:
stderr - W0718 13:30:43.182757 63070 warnings.go:70] would violate PodSecurity "restricted:latest": allowPrivilegeEscalation != false (container "vector" must set securityContext.allowPrivilegeEscalation=false), unrestricted capabilities (container "vector" must set securityContext.capabilities.drop=["ALL"]), restricted volume types (volumes "data", "var-log", "var-lib", "procfs", "sysfs" use restricted volume type "hostPath"), runAsNonRoot != true (pod or container "vector" must set securityContext.runAsNonRoot=true), seccompProfile (pod or container "vector" must set securityContext.seccompProfile.type to "RuntimeDefault" or "Localhost")
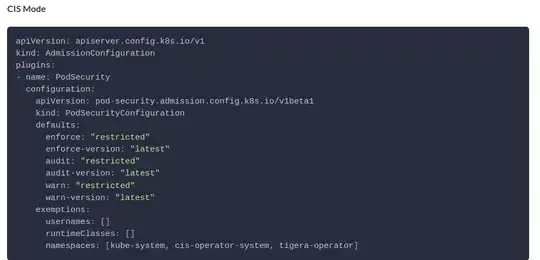
I presume that this is due the usage of the CIS Mode in RKE2 for the cluster. In this CIS Mode the Cluster runs with certain Pod Security Standards: https://docs.rke2.io/security/pod_security_standards
How can I solve this?