I have a problem that I cannot understand. This is my first question on this site, so in addition to downvote please tell me where I can improve the question.
On Windows Server 2022 I see several RDP attack each day, so I installed OpenVPN server.
OpenVPN Installation
- I installed and configured OpenVPN Server, for tunneling. Created private 10.8.0/24 network.
- I deactivated Firewall rules for opening RDP Port.
- I changed Firewall properties for not protecting "OpenVPN Tap-WindowsX". Without this step, the firewall blocks also traffic in private 10.8.0/24 network and no one could connect with RDP.
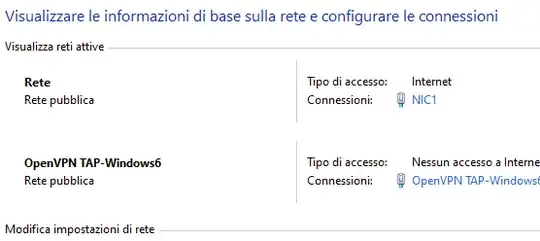
The Windows Network and Sharing Centre appear as following:
Firewall Configuration
The firewall is configured to block by default incoming connection in all the three profiles. I have excluded the OpenVPN Tap-Windows6 network from the firewall in all profiles.
I have some rules for allowing some port/programs, but I have disabled the RDP port rules. In fact I cannot connect with RDP with server public IP address:RDP port.
The problem
After installing VPN:
- I cannot access the server with RDP without VPN (I try to connect to public server IP address).
- I can access the server with RDP if I have OpenVPN Client already connected (I can connect to private server IP address).
Now, I still have RDP intrusion attempts, as seen in RDPGuard software. I have performed these checks:
- no one connected with VPN during the time of intrusion attempts, as seen in OpenVPN Server logs.
- attackers IP are not in 10.8.0/24 network.
I cannot understand how attackers by-passed the firewall. It seems they have a connection to a public IP address to a 10.8.0/24 network, but without an OpenVPN client connected how could this be done?
Firewall was configured to log only dropped packets, so I cannot see anything about RDP intrusion attempts.
Surely I have done something wrong, but I cannot figure what. Any suggestion is appreciated.
Thank You
--- Update 1 ---
After some investigation, with firewall configured for logging also permitted packets, I'm quite sure that the problem was port 135. After closing port 135 in the firewall public profile, I did not see any other intrusion attempt in RDPGuard.
I still cannot understand how an attacker can use port 135 to reach my RDP server, but I do not have a good knowledge of Windows RPC.
In particular for me is inexplicable that, in firewall logs, I cannot see the RDP port in the intrusion attempts.
--- Update 2 ---
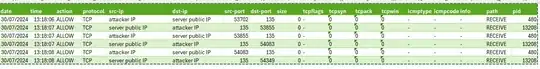
I can share the portion of firewall log for intrusion attempt. RDPGuard bans the IP after 3 failed login attempt and in the image above are reported these 3 failed login attempts.
Please note PID 13208 is RDPGuard and PID 480 is RPC Service (svchost).
Note also that no connections to the RDP Port is present.
@yagmoth555, I understand what you told me about layers, but now I configured the firewall to log also permitted packed, as you can see in the log extraction.
Even if firewall filters packets after RDPGuard, it has a chance to block/unblock the packet because if I don't exclude "OpenVPN Tap-WindowsX" network in the firewall properties, i cannot access with RDP.
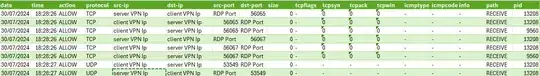
This is the log portion for a successfully RDP connection: (PID 9560 is Terminal Service)