I have an app running in a k3s cluster (flannel CNI). The app runs TCP+TLS requests in a loop and I've noticed that some of them are randomly timing out.
I've captured the traffic w/ tcpdump on the outgoing interface and I've noticed a pattern that repeats on every such timeout.
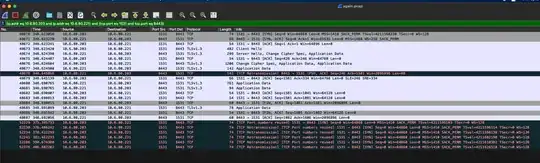
Below attached one of the conversations. I can see that there was a request (packet 48676), a response (packet 48680) and then connection closure (FIN, ACK -> ACK).
Although... the client keeps sending SYN for some reason which server won't respond to (connection is supposed to be closed). The application however waits and eventually timeouts.
is this pattern of packets familiar and known case?