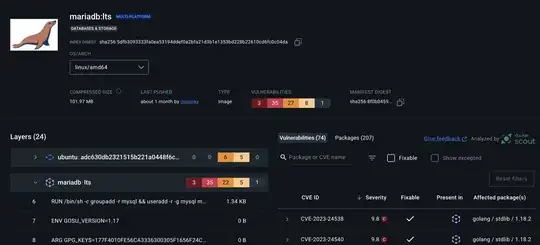
I found that the official mariadb images on Docker Hub have larger amounts of vulnerabilities (even 3 with severity critical). Most of them are caused by the package golang / stdlib / 1.18.2.
I observed this the stats now for several month and was hoping for a temporary problem (and that the numbers would eventually drop). However, the situation didn't get much better (according to the numbers). This really doesn't feel like I can run this and sleep well at night. Also the official mysql containers have this issue, so that's not an option either. So I was trying, what happens if I create a very basic custom container for MariaDB myself and see what docker scout quickview would report.
I created a very basic Dockerfile:
FROM ubuntu:24.04
RUN apt-get update
RUN apt-get -y upgrade
RUN apt-get -y install --no-install-recommends mariadb-server
CMD [ "/bin/sh", "-c", "sleep", "infinity" ]
did a docker build . and a docker scout quickview:
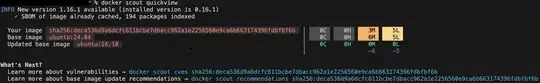
I wanted to use an OS officially supported by MariaDB (ubuntu 24.04 is supported, 24.10 is not according to MariaDB PLC Engineering Policy, Released on 2025-02-17). But, if we would be even a bit more adventurous we could use Ubuntu 24.10 and have 0 CVEs (same Dockerfile just replacing FROM ubuntu:24.04 with FROM ubuntu:24.10):
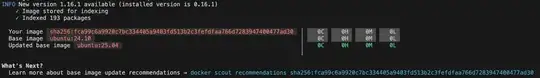
Of course the docker container might need some adaptions to the config files to be usable. And the mariadb-port needs to be exposed and so on. But, I believe I would not need any additional packages just to run a mariadb server microservice, that would introduce additional security flaws.
IDEA: I could build my own docker image for mariaDB and monitor it's via docker scout results (automatically each night) and maybe rebuild it from time to time (maybe also test it externally and push it to a docker registry, either self-hosted or private repo on hub.docker.com).
Given MariaDB should have been tested by the maintainers of MariaDB to work with this OS, there should be no real issues with Ubuntu 24.04.
QUESTIONS:
This leaves me with the following questions:
- Did I overlook something important?
- Is running this container (instead of the ready-made one) the safer option? Please explain why...
- Why is the
golang / stdlib / 1.18.2package in the official mariadb image at all? Might we be able to easily modify the image and uninstall this part by uninstalling an optional package?
Thanks for your time and support!