I am trying to create a internet distribution software for an ISP (an internet distributor or a school or other such organizations) like the one here
It will have restrictions and policies for users to limit bandwidth/speed/duration etc according to their internet connection package. Also, the administrator should be able to monitor their speed and block/allow users and renew packages.
The architecture is like:
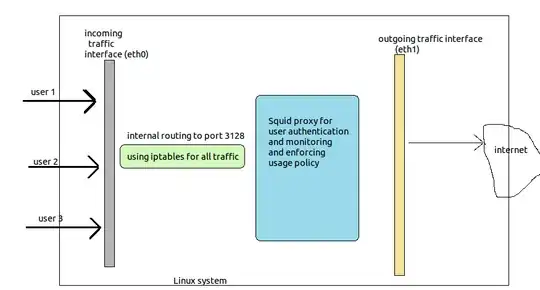
Non https client request work fine. But https request are giving SSL_ERROR as expected.
I read Squid cannot handle https connections in transparent proxy mode, but I do not want users to set proxy in their browser every time.
Is there any other way so that we can count all the traffic, including the encrypted traffic, used by a user and shape the traffic accordingly?