I'm the resident IT guy in an office with about 20 workers, amongst 3 separate companies who sublet an office.
We are wired with 24 ethernet ports dotted around the offices that all lead to a patch panel in my office. They are connected to 4 unmanaged switches into our ISP-supplied, cheap, router. (Internet is provided by a regular ADSL2+ provided by BT in the UK).
The problem is we are all one network, despite being separate companies, which is a security concern so we want to separate the logical/virtual networks (presumably, VLANs), but our current basic router doesn't support port-based VLANs.
I'm consider two options to isolate the networks, and I'd like advice which will do the trick:
A enterprise 4-port router (perhaps a Zyxel P660HN-51 or Draytek Vigor) that supports port-based VLANs, and plug our existing unmanaged switches into that:
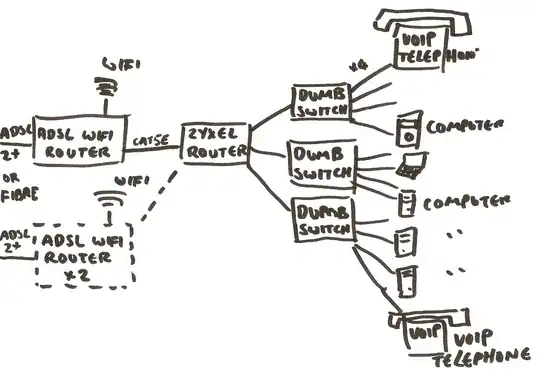 (obviously, I would restricted to 3-4 VLANs, but that's fine
(obviously, I would restricted to 3-4 VLANs, but that's fineOr, a large 24-port managed switch (like a Cisco), that supports allows me to define which of it's many ports belong to which VLANs.
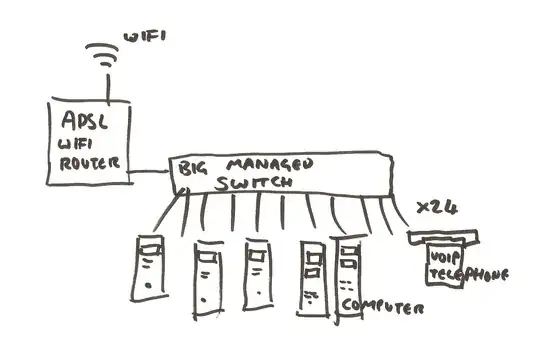 I understand that this can just work in a "router-on-a-stick" configuration. Crucially, my network cupboard is too small to fit a typical 24 port switch, It's only got about 22cm depth.
I understand that this can just work in a "router-on-a-stick" configuration. Crucially, my network cupboard is too small to fit a typical 24 port switch, It's only got about 22cm depth.