I tried a myriad of approaches none of which worked. But one did
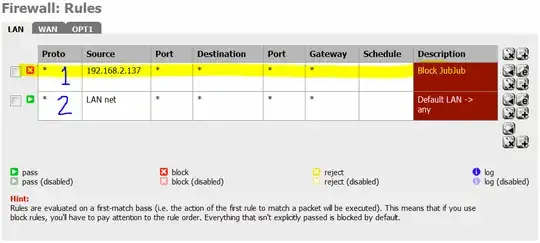
(a)I first set up a rule that would allow (in this case 192.168.1.7) to connect to anywhere in my 192.168.1.0 /24 lan. So that means
Firewall--> Rules--> Edit
- Action -->Pass
- Interface --> LAN Address
- Family -->(you choose)
- Protocol --> Any
- SOURCE Single Host ---> 192.168.1.7
- Destination ---> Network 192.168.1.0 /24
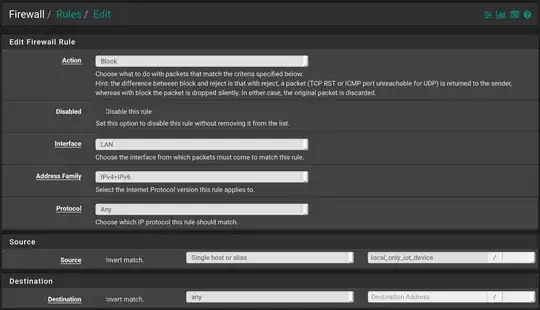
(b) Next I created a block rule below this one in the hierachy of
Firewall-->Rules-->Edit
- Action --> Block
- Interface ---> LAN
- Address Family ---> (user choice)
- Protocol --> Any
- Source Single Host or Alias ---> 192.168.1.7
- Destination --> any
That worked
What is really confusing is the terminology. Perhaps someone can explain this
(a) If I have an IP address on my internal LAN then why wouldn't blocking it to access the WAN (which is outside my router and I would think would be considered the Internet) block that IP address from accessing the Internet
(b)So why does blocking that IP address from accessing the LAN (I suppose that any IP address behind the NAT is on the LAN and any IP in this network behind the LAN can reach out to the Internet unless it is blocked) prevent that IP from accessing the Internet. I suppose I just answered my own question because the next thing I did was allow that IP address to access the local network 192.168.1.0 /24 (in CIDR format)
I will say that the terms LAN, WAN Network etc need a little clarification for noobs using pfSense. What is the WAN, really ? Why can't I just block my lan ip address from accessing the WAN ? Why does that not work? I think anyone who can answer that question would help me and a lot of others, I would guess
Thanks, parry