I run a site with about 700 registered users. On a typical day, there are 30-50 hits.
In the last three days, the traffic has increased insanely fast (according to Google Analytics). I got 7,287 hits today. My number of new registered users has not increased proportionally.
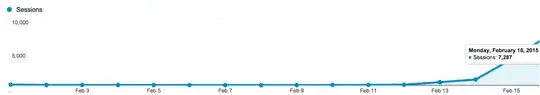
It seems that the majority of them are from Russia, which is funny because I'm in the US and my site is English only.
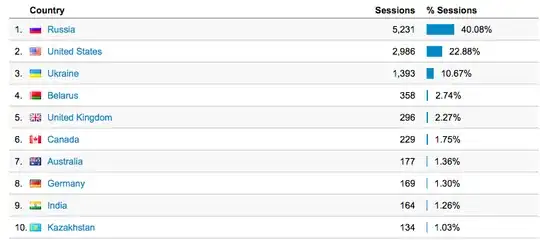
Now, I've done some Googling to check out what's up with all these referral links in Google Analytics.
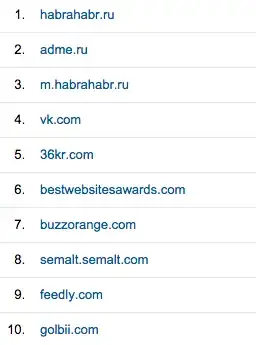
I've read that most of those are just Russian referral spam hits, in which someone has scraped my Google Analytics key from my HTML, and then they just hit Google Analytics thousands of times to annoy me without actually requesting anything from my server (which is fine, but I think it makes Google Analytics barely valuable at all anymore, because now my data is polluted, but that's besides the point...).
However, my Nginx logs show a significant increase in the amount of traffic during the last few days. The Russian referral spam hits account for only about half of the total number in Google Analytics. I honestly can't figure out why someone would just hit my site over and over again, it takes human interaction to get any meaningful content out of my site.
What can I do to protect myself from this illegitimate traffic? Is my only option to start blacklisting IP addresses?