I'm new to AD and Windows Server, and this sounds like it should be pretty obvious, but I can't seem to figure out the distinction between a tree and a forest.
According to the book I'm reading: Active Directory For Dummies:
To put it simply, you create a forest only if you need to use more than one namespace. If you require more than one namespace because you require more than one naming structure, you need to plan an additional tree for each namespace.
The book also provides this diagram:
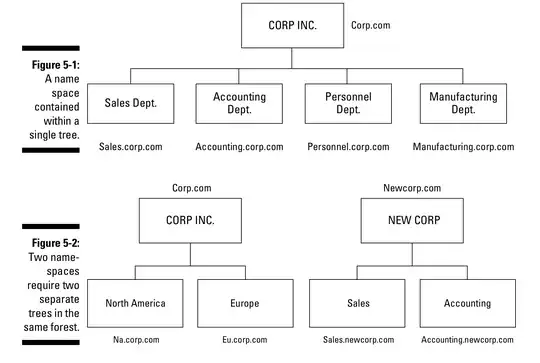
I don't completely understand the statement, but according to the diagram, if you have Corp.com and Newcorp.com, you should have 2 trees in the same forest as opposed to 2 different forests. According to this however:
Windows Active Directory naming best practices?
the main recommended way of naming your "AD", by which I assume they mean forest, is:
- An unused sub-domain of a domain that you use publicly. For example, if your public web presence is
example.comyour internal AD might be named something likead.example.comorinternal.example.com.
Using the recommended way, if you name your active directory ad.Corp.com and later need to add ad.Newcorp.com to your forest as a new tree, it seems like it's going to be pretty weird since ad.Newcorp.com will be a tree in a forest named ad.Corp.com.
What am I missing here?
Edit:
According to https://www.youtube.com/watch?v=Whh3kPS0FdA, you would mostly only need a new forest if you:
- Merge with another company whose AD forest has a different schema than yours
- Are testing an application that makes changes to the schema, and you don't want it to effect your production schema
My biggest problem is this: What would you name your forest so that even if you add different DNS namespaces later (like adding NewCorp.com), you don't end up with a forest named Corp.com with a tree named NewCorp.com, or something even weirder? And if a forest can contain multiple DNS namespaces, why is it recommended to name it something like ad.example.com instead of something generic?
Edit 2:
The same book suggests using something generic like AD.LOCAL as the name of the forest root domain, which makes sense, as this would allow you to have multiple DNS namespaces. Using SOMETHING.LOCAL is no longer considered a good name for a forest root domain however, so how does the new suggested naming convention handle different DNS namespaces?