Situation:
Running PsExec takes 20 seconds with the Windows firewall active, and 1 second with it disabled.
Exceptions added to the firewall:
- opened ports 135 and 445 (both tcp) as per http://jamesrayanderson.blogspot.co.uk/2010/04/psexec-and-ports.html
- "allow app through firewall" choose "Remote Service Management"
- ensure network is set to private
Without these two it won't connect at all. Target machine running windows 10. During the 20 second wait it sits saying "Starting PsEXESVC on "
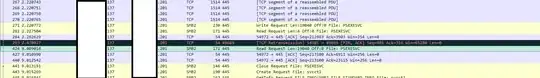
A little wiresharking shows us that we need to also open another port which is being requested.
- first time I ran this it was 49669 second time it was 49670
No idea why nor what range it will accept, any ideas?
Is there a definitive list of what ports PSEXEC needs to have opened?