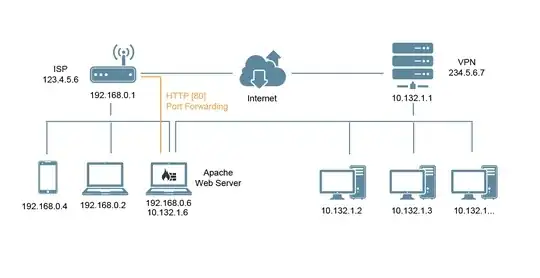
I have an apache server that works perfect until I connect to VPN and then all connections to server time out.
Now to my understanding the issue is tun0 becomes the default output interface hence apache gets confused as how to send packets out, so I tried to fix it using control groups by marking packets going out from apache and redirecting them through eth0 as described in this SU answer, but it doesn't work anymore after I upgraded my Ubuntu OS to version 16.04. This is my network diagram:
And here's my network details:
me@mypc:~$ ip route list
0.0.0.0/1 via 10.132.1.5 dev tun0
default via 192.168.0.1 dev eth0 proto static metric 100
10.132.1.1 via 10.132.1.5 dev tun0
10.132.1.5 dev tun0 proto kernel scope link src 10.132.1.6
123.4.5.6 via 192.168.0.1 dev eth0
234.5.6.7 via 192.168.0.1 dev eth0
128.0.0.0/1 via 10.132.1.5 dev tun0
169.254.0.0/16 dev eth0 scope link metric 1000
192.168.0.0/24 dev eth0 proto kernel scope link src 192.168.0.6 metric 100
me@mypc:~$ ifconfig
eth0 Link encap:Ethernet HWaddr 00:cc:a9:b3:c9:41
inet addr:192.168.0.6 Bcast:192.168.0.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:864897 errors:0 dropped:0 overruns:0 frame:0
TX packets:467142 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1088053099 (1.0 GB) TX bytes:220201868 (220.2 MB)
Interrupt:17
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
...
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.132.1.6 P-t-P:10.132.1.5 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:46622 errors:0 dropped:0 overruns:0 frame:0
TX packets:14950 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:60587170 (60.5 MB) TX bytes:1396546 (1.3 MB)
I've done further testing and discovered that if I add this routing rule:
sudo route add -host 123.4.5.6 gw 192.168.0.1
I become able to connect to the server from devices connected to my router using the router ip 123.4.5.6 but not from any other ip address.
And after setting up the control groups on apache and trying the following command:
sudo cgexec -g net_cls:novpn wget http://www.whatsmyip.org/
and checking the ip in the downloaded webpage it would be my router ip 123.4.5.6 and not my vpn ip 10.132.1.6.
So I guess the control groups solution works somehow but not with apache and the incoming packets are being received successfully by apache but nothing is going out.
How can I configure apache to use eth0 to output packets instead of tun0?