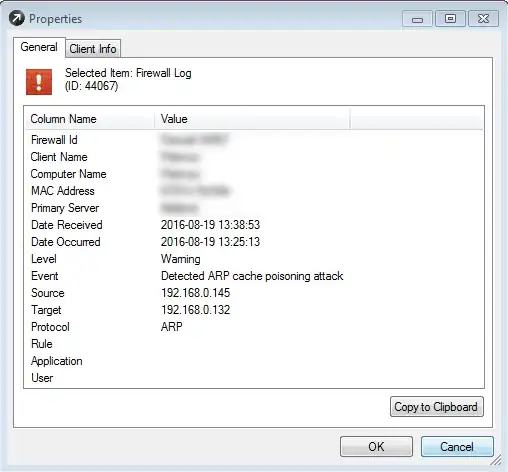
If these devices have multiple network interfaces which have an IP address in the same subnet, then it is possible that your are suffering from ARP Flux:
When a linux box is connected to a network segment with multiple network cards, a potential problem with the link layer address to IP address mapping can occur. The machine may respond to ARP requests from both Ethernet interfaces.
On the machine creating the ARP request, these multiple answers can cause confusion, or worse yet, non-deterministic population of the ARP cache. Known as ARP flux [13], this can lead to the possibly puzzling effect that an IP migrates non-deterministically through multiple link layer addresses.
It's important to understand that ARP flux typically only affects hosts which have multiple physical connections to the same medium or broadcast domain.
If you have a system which detects when IP > MAC address mappings are changing, a device which announces two different MAC addresses for the same IP address could cause this system to trigger.
As a test, you can modify the arp_ignore sysctl variable on the interfaces and see if that stops the warnings. Setting the value of that variable to 1 (default 0) will ensure that only the interface which holds the target IP address of the ARP request will respond.
To modify the value temporarily, set the variable for each of your interfaces. For example:
echo 1 > /proc/sys/net/ipv4/conf/all/arp_ignore
echo 1 > /proc/sys/net/ipv4/conf/default/arp_ignore
echo 1 > /proc/sys/net/ipv4/conf/eth0/arp_ignore
...
echo 1 > /proc/sys/net/ipv4/conf/eth6/arp_ignore
The changes above will be reverted on reboot, so if it resolves your issue you can make the change persistent by adding a new sysctl conf file:
user@host: ~$ cat /etc/sysctl.d/90-no-arp-flux.conf
net.ipv4.conf.all.arp_ignore=1
net.ipv4.conf.default.arp_ignore=1
net.ipv4.conf.eth0.arp_ignore=1
net.ipv4.conf.eth1.arp_ignore=1
Load the new conf file with sysctl -p /etc/sysctl.d/90-no-arp-flux.conf