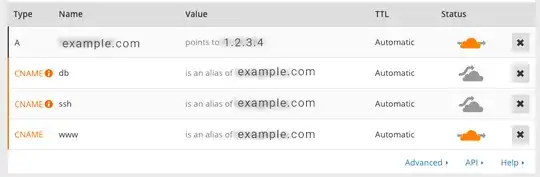
We have installed on one server a regular web-site (http://example.com) and web-mail (https://example.com/mail), Debian, Joomla, NGINX, iRedMail.
For protection from DDoS we use CloudFlare in free variant.
So the problem is: when CF is turned off everything is OK - site and web-mail is accessible. But when turning on CF-protection - site is OK, but web-mail says "too many redirects" in SSL.
Tried to set up as described here - nothing changes.
Seems like some misconfiguration in redirection rules in CF rules, or ngnix - can't understand. But where?
/etc/nginx/sites-enabled/example.com (web-site):
server {
listen 80;
server_name example.com;
server_name_in_redirect off;
root /var/www/example.com;
index index.php index.html index.htm default.html default.htm;
location / {
try_files $uri $uri/ /index.php?$args;.
}
location ~* /(images|cache|media|logs|tmp)/.*\.(php|pl|py|jsp|asp|sh|cgi)$ {
return 403;
error_page 403 /403_error.html;
}
location ~* \.(ico|pdf|flv)$ {
expires 1y;
}
location ~* \.(js|css|png|jpg|jpeg|gif|swf|xml|txt)$ {
expires 14d;
}
include /etc/nginx/templates/php-catchall.tmpl;
include /etc/nginx/templates/redirect_to_https.tmpl;
include /etc/nginx/templates/misc.tmpl;
}
/etc/nginx/sites-enabled/example.com_443 (web-mail):
server {
listen 443;
server_name mail.example.com;
ssl on;
ssl_certificate /etc/ssl/certs/iRedMail.crt;
ssl_certificate_key /etc/ssl/private/iRedMail.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-R
ssl_prefer_server_ciphers on;
ssl_dhparam /etc/ssl/dh2048_param.pem;
index index.php index.html;
location / {
root /opt/www/roundcubemail;
}
# Web applications.
include /etc/nginx/templates/roundcube.tmpl;
include /etc/nginx/templates/iredadmin.tmpl;
include /etc/nginx/templates/php-catchall.tmpl;
include /etc/nginx/templates/misc.tmpl;
}
CF Rules:
https://example.com/mail SSL:Flexible - Full
When enabling CF protection of example.com (DNS A-record) mail.example.com falls into a redirect loop.