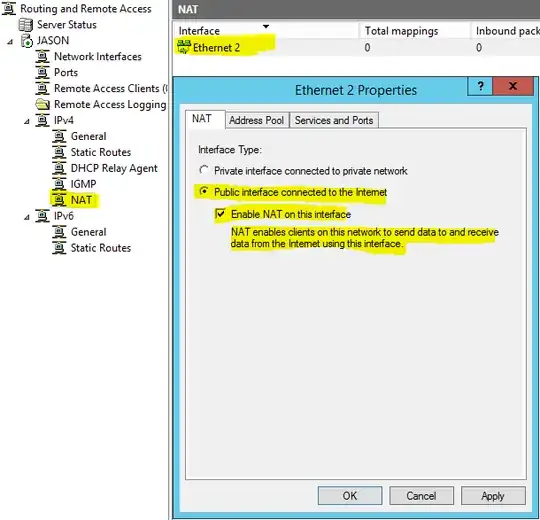
Its not a NAT issue. What is probably going on is that the IP configuration you are getting from the VPN is what is affecting. You need to have DHCP and DNS configured on your server and have your VPN forward/relay the DHCP scope to your VPN.
This is the properties of my VPN:
Click to view picture
Here, notice the block reserved for RAS, this shows that some addresses have been reserved for your VPN and the relay is working and any PC that connects to your VPN should get an address automatically.
Click to view picture
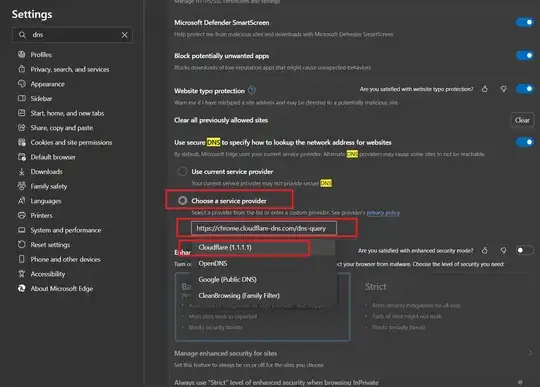
If you dont want to setup a DNS server, then in your DHCP configuration you can have google's public DNS as the DNS server.
I encountered this exact same issue when setting up my SSTP VPN.
UPDATE:
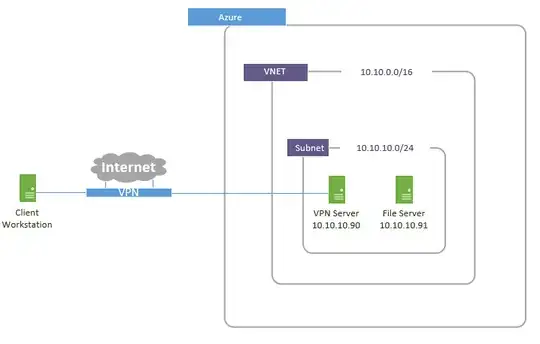
Looking at your network, is the subnet 10.10.10.xxx being "natted"? If it is, then it could be that youre trying to access the server behind a second NAT, assuming the 10.10.0.0 subnet IS a NAT itself. If it isnt, then port forwarding 443 from Azure to your server should do the trick along with the above i posted.