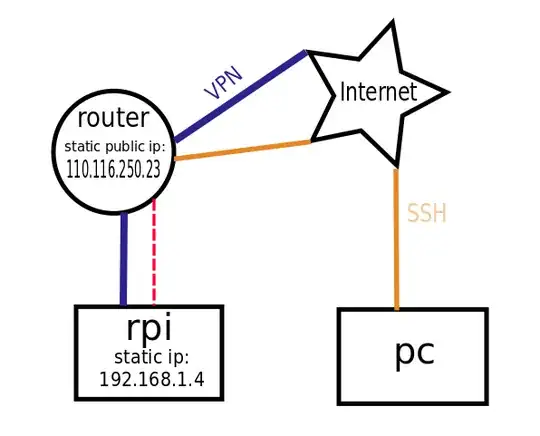
I have a Raspberry Pi server (rpi) with a static internal IP using a VPN service. My router has a static public IP and I have the NAT set up to forward SSH traffic to the rpi as I have other devices on the network.
I am able to SSH into the rpi server remotely (out of my network) when no VPN is used. I am able to SSH into the rpi internally (in my network) when the VPN is used. I am not able to remotely SSH into the rpi when the VPN is used.
I have seen other questions that are similar but I'm such a novice I couldn't quite understand fully what was explained or ascertain if the situation was the same as mine.
I don't believe I'm using a firewall on the server but am relying on the router to block connections and using NAT to forward connections. I don't understand what iproute is for or on which machine it should be configured.