On my AWS Lambda function, my javascript code times out whenever I try to use nodemailer to connect to my Amazon SES SMTP server (port 465). However, if I run the script locally, it works fine, which leads me to believe it's either a problem with the lambda dialing out to the SMTP server, or the SMTP server blocking the lambda from connecting -- I suspect the former is the issue.
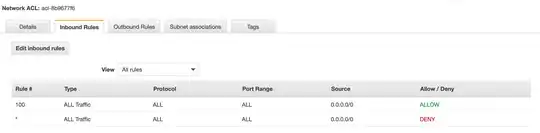
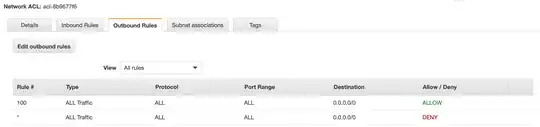
I am using a firewall behind my Cloudfront distribution, but I don't think this is applied to incoming SES connections or outgoing lambda functions. In VPC, I can see there is an Internet Gateway attached to the instance. The outgoing connections for the Security Group allows all protocols to access 0.0.0.0/0, however, the ACL looks odd in that it's both allowing and rejecting all inbound/outbound connections:
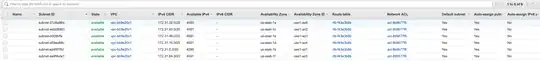
In VPC, I see 6 subnets listed, where it's not very obvious to me what exactly these are doing in the grand scheme of things.
In the logs, I just see Task timed out after 6.01 seconds
Any idea how I can get more information on where the hangup is at?