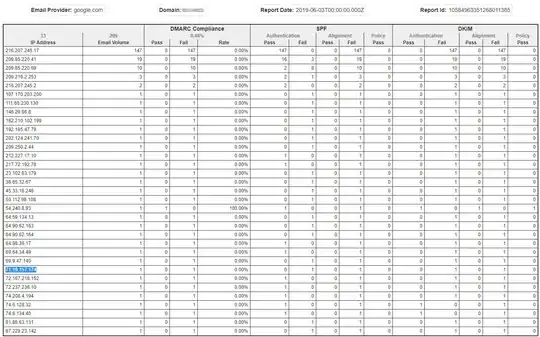
An example from your DMARC report:
Host 216.207.245.17 (reverse lookup tells us lists.digium.com) sends 147 emails on behalf of your email domain. These emails PASS an SPF check, but, since the domain used for the SPF check does not align with your email domain, it fails in regards to DMARC.
Especially email forwarders / mailing lists behave this way. Before distributing the email to the members of the list, the bounce address (aka smtp.mailfrom / return-path / envelope from address) is re-written, so that Non-Delivery Reports (NDRs) are sent back to the mailing list provider and not to the original sender.
While the FROM address is shown to the recipient in the email client, the envelope from address is hidden, but IS used to check the SPF on. This is why DMARC is so important to protect against phishing, because SPF (or DKIM) alone does not authenticate the FROM address the recipient sees.
The way mailing lists typically behave will fail DMARC authentication on SPF check, because the alignment between envelope from domain and FROM domain is removed. Also, sometimes DKIM signed fields such as subject are edited, which breaks the original DKIM signature.
This is exactly why ARC (Authenticated Received Chain) is being created, as an extension to DMARC. Unfortunately, ARC is still in Draft stage.
So if we look back at our example, the mailing list provider re-writes the envelope from address to something@lists.digium.com and the receiving mail server checks the domain lists.digium.com for an SPF record, which it finds: "v=spf1 a mx ip4:216.207.245.0/26 ~all\". SPF passes (216.207.245.17 is part of range 216.207.245.0/26), DMARC fails. Depending on your DMARC policy action and receiving server configuration, the email may be marked as SPAM, quarantined, rejected or delivered to the Inbox.