I was signing up for a website last night, and once again was greeted with the fact that my username cannot contain certain characters (including spaces)
A lot of websites use usernames as keys to lookup records in a database, and traditionally keys don't have spaces. As for special characters that can be a wide range of reasons why they are excluded. The owners of the site simply might not want people named $%@#$% as a user.
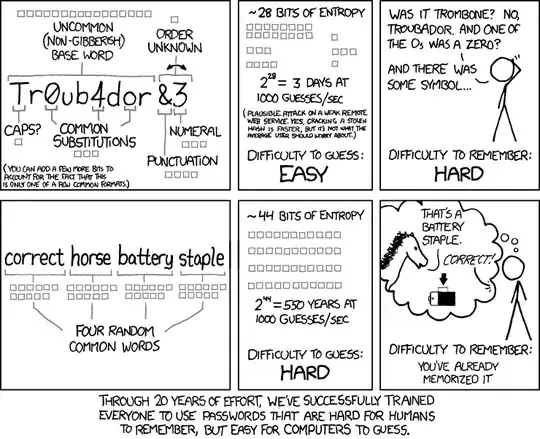
Passwords that are phrases have higher entropy and are harder to crack than simple letter/number substitution:
That is a bias perspective from your point of view, and keep in mind that passwords are not cracked but websites are cracked.
Long form passwords based upon phrases actually make it easier to decrypt a hashing algorithm, then a short password containing upper, lower characters, numbers and special characters. The reason is that human language uses far fewer of the letters in the alphabet for most phrases. This allows a hacker to narrow the scope of their attack on a hash. If they know all passwords are 8 characters, but contain a possible range of 255 different characters than that is a massively huge range of possible hashes.
The most common attack on a website does not come from that website. It comes from weaknesses in another website. If I hack into website ABC and get a list of unhashed emails and passwords, then I can use that list to attack other websites.
Before a hacker uses his list on popular websites like Facebook, Twitter or Google. They will clean that list by attacking smaller websites to see which idiots re-used their passwords. Once they have a cleaned list the odds are that person re-used the password on a major website.
Often those websites are attacked without the attacker ever being noticed, because they walked right in using valid authentication.
So never re-use your password. Always use a randomly generated one and stop using phrases.
Use A Password Vault