Backstory
I am writing a library that accesses the kernel module, uinput which allows you to create or take control of devices in /dev/input/event#, and insert events into them.
A simple usecase would allow someone to write a script that would move a mouse cursor to the center of your display, and perform a left click.
As such, it needs root priveleges in order for it to function, and I am not sure what tangible risks I am taking here, and exactly what precautions I need to employ.
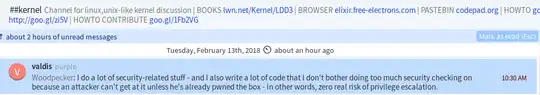
I asked about this in ##kernel, and one response I got was:
Questions
- Is what he says true, that my library will be fine to the extent that my system is not "pwned"?
- To that, how do I know my library will not become a vector for my system to be "pwned"? I am not a hacker so I would not know what exposes my library to such a thing.
- I want my code to be presentable to potential employers, so even if it is true that I need not worry, what security practices should I employ just to demonstrate that I am astute and conscious of potential security risks?
- Would a best practice in this case involve me creating a user with a special permission group that limits his exposure to the system?
Thanks.