I came up with an model to reduce DoS and DDoS attacks and would like your input on its effectiveness...
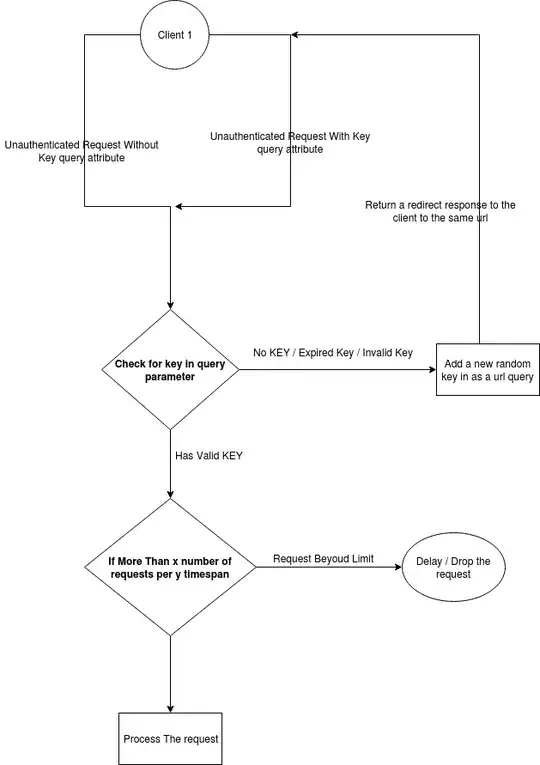
Basically, once a request reaches our servers without having a valid key, we add a key as a query parameter of the url, then return a redirect response to the client with the same url but with a valid key.
Then we can use this key to throttle the requests instead of using an IP Address.
I understand that the attacker might still make millions of new requests to the server, but redirecting the client should be fairly lighter than say downloading a video or large file.