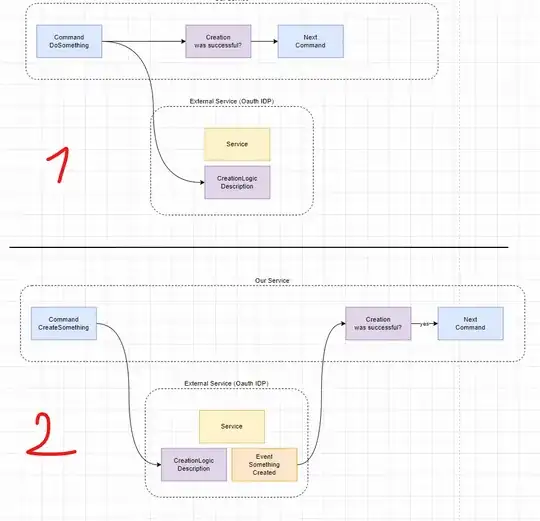
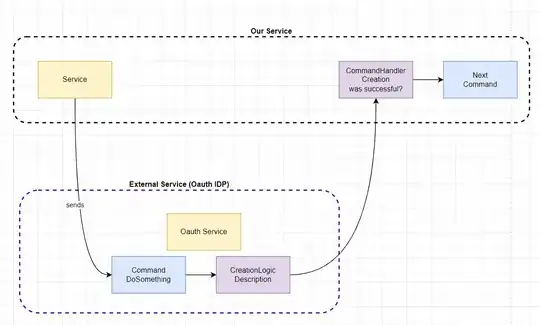
I have a discussion with a colleague regarding how to model a command that immediately gets an answer to it's HTTP POST request back. In this specific case we do an API call to a 3rd party IDP API that we don't control, we'll do a HTTP post and get a response.
There are two statements from him regarding this:
- Event Storming is NOT about implementation.
- We want to do EDA, therefore we MUST use events everywhere.
The first one MIGHT be true, but the implementation then has to follow the process somehow and therefore I think they are equal.
The diagram (2) below is wrong in my opinion because the HTTP response is not an event and the follow-up action is NOT triggered by an event but the outcome of the HTTP call, which is, by its nature async, but from the perspective of the system it is still a process that requires a specific execution order and relies on the immediate outcome of the request.
However, I'm not happy with (1) in the diagram either. So how do you express that the immediate result of a command is the condition to proceed with the process and not an event? Is that at all correct?